TLS Handshake Sequence Explained
The TLS handshake is a cryptographic protocol used to securely establish an encrypted connection between a client (like a browser) and a server (like a web API).
This handshake negotiates everything needed to protect communication: encryption keys, supported algorithms, authentication, and integrity checking.
TLS Handshake Flow
| Step | Description |
|---|---|
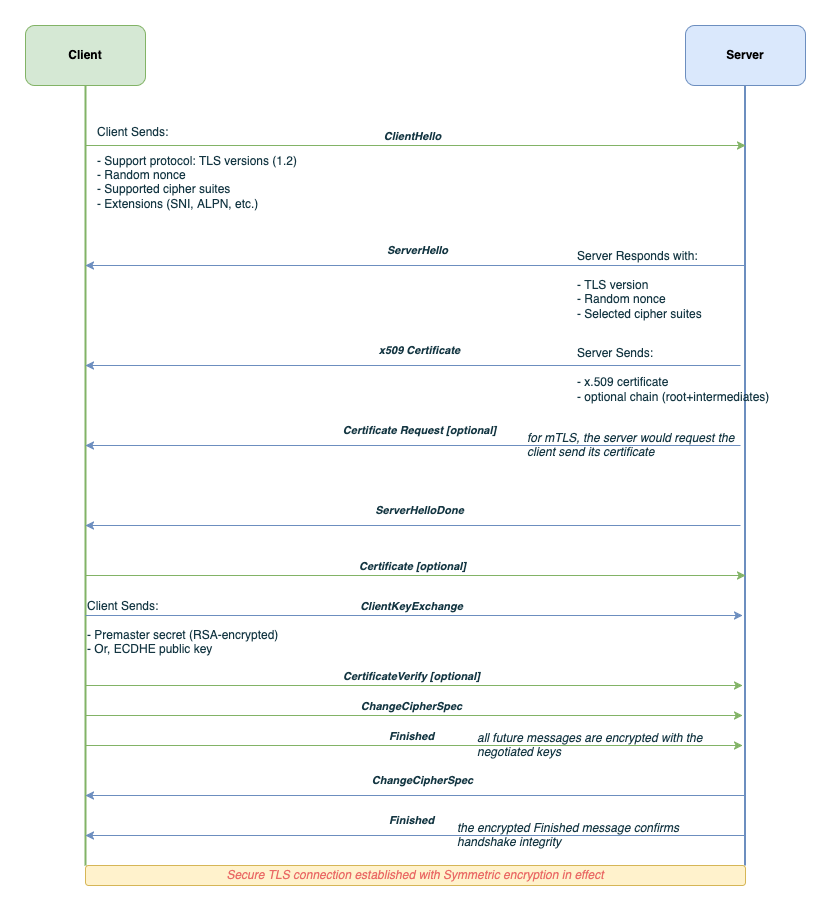
ClientHello | Client initiates handshake, offering TLS version, supported cipher suites, random nonce, and extensions like SNI or ALPN. |
ServerHello | Server responds with chosen cipher suite, version, and its own nonce. |
Certificate | Server sends its X.509 certificate to prove identity. |
[Optional] CertificateRequest | Server may request a certificate from the client (used in mutual TLS). |
ServerHelloDone | Indicates server is done with its part of the handshake. |
[Optional] Certificate | Client sends certificate if requested. |
ClientKeyExchange | Client sends the premaster secret (e.g., RSA-encrypted or ECDHE public key). |
[Optional] CertificateVerify | Client proves possession of the private key. |
ChangeCipherSpec | Client and server signal that future messages will be encrypted. |
Finished | Each party sends an encrypted message digest of the handshake. |
| Secure Channel Established | Symmetric encryption is now active for all future communication. |
Key Concepts
| Concept | Explanation |
|---|---|
| Cipher Suite | Defines which algorithms will be used for encryption, key exchange, and MAC. |
| Random Nonces | Random values from both sides, used to derive shared session keys. |
| Pre-Master Secret | A value generated by the client, sent to the server and used to derive the symmetric keys. |
| Certificate (X.509) | Server’s digital certificate, proving its identity and containing the public key. |
TLS Handshake Sequence Diagram
What Happens After the Handshake?
- A shared symmetric key is derived from the exchanged data.
- All future communication is encrypted, authenticated, and tamper-proof.
- The handshake is relatively expensive; session reuse or TLS 1.3 can reduce round trips.
How to Inspect a TLS Handshake
Run this from your terminal to observe a real handshake:
openssl s_client -connect example.com:443